Are Next GEN Firewalls still relevant? Since the early 90’s, I saw firewall manufacturers progressively deploy features after features on their firewall appliance to differentiate themselves from the competition. Some notable technologies were UTM (Unified Threat Management) and “Next Gen” firewalls. Today, manufacturers use terms such as “Security Fabric” and introduce Artificial Intelligence to help with their product sales.
But are all these new innovation really useful? I much confess that I find these built-in gadgets less relevant simply because contrary to 10-20 years ago, more traffic flowing thru a firewall is already encrypted at the application layer, rendering the security scan tools of the firewall blind to packet contents.
Of course, some firewall will look at the packet headers to get a hint of how to process this packet against its security policies, but it can’t inspect the encrypted portion of the packet.
One of the many challenges I had to resolve was moving many of our organizations services to the cloud. Firewall manufacturers slowly replaced UTM functionality with various service objects which made it much easier to create policies for cloud services. but needs to be updated constantly by the manufacturer thru a subscription service.
In the early 2000′ UTM (Unified Threat Management) found it way into our vocabulary and sparked a resurgence of interest because of firewall’s capability to nip bad packets in the bud. The term “UTM” is not a standard per say, but a term describing the capability of the firewall to manage multiple security oriented features. When security slowly became a topic of discussion rather than something you ignored, several firewall manufacturers leveraged the opportunity to introduce enhanced security tools and services, on top of their typical VPN, firewall policies, routing capabilities.
One of these manufacturers was an upcoming new player and had a secret weapon, the application-specific integrated circuit (ASIC) architecture. This chip allowed its firewall product to outperform it competition 10:1 in many cases and at relatively the same price point. The company which had that capability was Fortinet.
In 2004, I adopted the next generation of UTM firewalls to protect the assets of the company I was working for. The term UTM (Unified Threat Management) was the new industry buzz-word and firewall manufacturers were in a race to pack as many security features inside their firewalls as they could, and cash in on a new source of revenues: subscription and support fees. You see, getting updates to the library of malignant viruses or intrusion signatures required constant updates from the manufacturers, which were offered as a yearly service.
These security features came in the form of realtime intrusion detection (IDS), intrusion protection (IPS), anti-virus (AV), denial of service attack prevention (DDOS), anti-spam mail engines and many other security orient features. At those days, I was managing an ISP network and had front-row-center visibility to all internet uplinks.
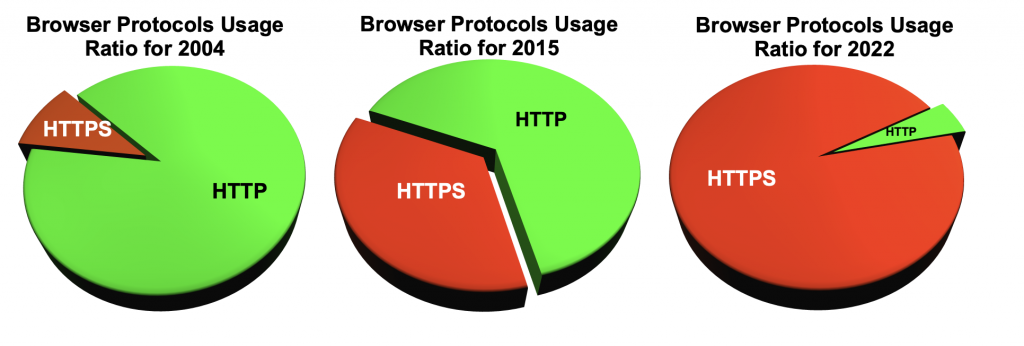
One day, I wanted to measure the top used protocols on this ISP. Using a packet sniffer, I tapped into the IPS uplinks and measured the percentage of each protocols. By order of volume, HTTP was by far the most used protocol, then SMTP came in second place and finally HTTPS, FTP, POP3, IMAP came in 3rd,4th,5th and 6th place and the remaining measured protocols not used very often. This was before video/audio streaming became popular and most people still used 56k modems on voice phone lines.
Since HTTP was transmitted in clear text, it UTM equipped with made short work of scanning packets flying thru the appliance, and depending on the policies, made the appropriate choice of ignoring or blocking. UTM were efficient and pretty reliable, but not fool proof.
Between 2004 to 2020, UTM engines became progressively less relevant since they couldn’t read fast growing encrypted protocols. In 2018, web browsers began “flagging” websites still using HTTP as “Not Secure” and initiated the coup-de-gras for HTTP. Nobody wanted to use something which was not secure and the race to use secure sockets layers (SSL) was at a point of no return.
This trend not only applied to web browser, but other protocols such as FTP (File Transfer Program), and SMTP (Simple Mail Transport Protocol) we also offering end-to-end encryption solution during transport. Many web based services like Facebook, WebMail, Youtube also migrated toward an SSL based protocol and UTM slowly lost their raison-d’être.
Here is the approximate ratio of web browser protocols used in 2004, 2014 and 2022.
In an effort to adapt to this new trend of encrypting everything and to keep the flow of revenues for their UTM appliances, manufacturers started innovating and offering new firewall features to essentially trick the browser into accepting a substitute security certificate, and in a sense, letting the supposedly encryption data payload travel un-encrypted while traversing the firewall. This allowed UTM to regain some visibility and allow it to use intrusion and protection mechanism again.
This approach wasn’t successful simply because the inter-working of some secure website would not allow certificate substitutions and refuse to work when it detected a “man-in-the-middle” connection.
Implementing a proxy, or, man-in-the-middle system on a firewall is now becoming an Ethic or Legal issue rather than a technical one. Depending on the region you are in, it may illegal to decrypt protocol to look at the data being transported. If it doesn’t fall under legal issue, it may very well go against your own internal security policies.
In conclusion, UTM & Next Gen firewall have lost their luster when it come to content inspection. New functionalities, such as SD-WAN, Load Balancing and Smarter Routing Protocols are replacing UTM tools. Manufacturers still propose such UTM tools with their product, but realistically, they just don’t have the impact they once had before. I would qualify “Web URL filtering” to be the UTM functionality that is still valid today, when you can block HTTP/HTTPS access to remote sites based on URL categories. WAF (Web Application Firewall) is also probably the most usefull firewall subscription service which has been implemented during the past 5 year or so. WAF also allowed to migrated some corporate services to the cloud. Fortinet, for example, introduced a subscription service which allows to put cloud services IP in categories, and allow firewall admins to quickly and accurately create policies to allow access to many popular cloud services.
If you are still applying IDS/IPS/AV on your firewall traffic policies, you are probably wasting your firewall’s resources. If you are paying for a subscription service for IPD/IDS/AV, you are probably wasting your money. You would be better have Logging traffic to a SIEM and spend on EDR (Endpoint Detection and Response).
This was my point of view.
Cheers and Beers.

