 Cybersecurity is a complex and dynamic field that involves protecting various systems, data, people and more from malicious or negative events. To understand the challenges and solutions of cybersecurity, it is important to know the basic concepts of threat, asset, vulnerability and risk. These terms are often used together, but they have distinct meanings and implications.
Cybersecurity is a complex and dynamic field that involves protecting various systems, data, people and more from malicious or negative events. To understand the challenges and solutions of cybersecurity, it is important to know the basic concepts of threat, asset, vulnerability and risk. These terms are often used together, but they have distinct meanings and implications.
An asset is anything that has value to an organization or an individual, such as a computer, a database, a website, a customer record, a trade secret, a reputation, etc. Assets can be tangible or intangible, physical or digital, and they can vary in their importance and sensitivity. For example, a bank may consider its customer data as a critical asset, while a blogger may value their online presence more.
A vulnerability is a weakness, flaw or other shortcoming in an asset’s design, implementation, operation or management that could be exploited by a threat. A vulnerability can exist in a system (infrastructure, software or hardware), a process, a set of controls, or simply the way that something has been implemented or deployed. There are different types of vulnerabilities, such as technical vulnerabilities (bugs in code or errors in hardware or software), human vulnerabilities (employees falling for phishing, smishing or other common attacks), or organizational vulnerabilities (lack of policies, procedures or training). For example, a vulnerability could be leaving a door unlocked, using a default password, or having outdated software.
A threat is a potential for a threat agent to exploit a vulnerability, which could affect the confidentiality, integrity or availability of an asset. A threat agent is any person, group, entity or circumstance that has the capability, intention and opportunity to cause harm. A threat can be intentional or unintentional, malicious or benign, active or passive, internal or external, and it can vary in its likelihood and impact. For example, a threat could be a hacker, a virus, a natural disaster, a power outage, or a human error.
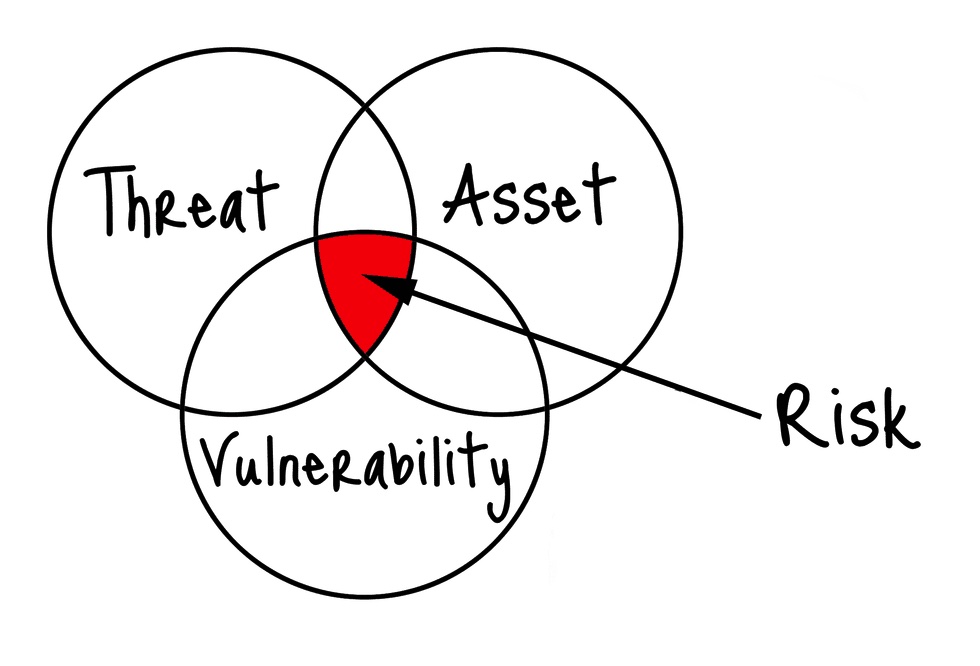 A risk is the potential for loss or damage when a threat occurs. Risk is a function of the likelihood and impact of a threat exploiting a vulnerability, and the value of the asset. Risk can be measured in terms of probability and severity, and it can be expressed in qualitative or quantitative terms. For example, a risk could be losing money, data, reputation, or customers.
A risk is the potential for loss or damage when a threat occurs. Risk is a function of the likelihood and impact of a threat exploiting a vulnerability, and the value of the asset. Risk can be measured in terms of probability and severity, and it can be expressed in qualitative or quantitative terms. For example, a risk could be losing money, data, reputation, or customers.
The relationship between these four concepts can be illustrated by the following formula:
Risk = Asset x Vulnerability x Threat
This means that the risk level depends on the value of the asset, the presence and severity of the vulnerability, and the likelihood and impact of the threat. To reduce the risk, one can either decrease the value of the asset, eliminate or mitigate the vulnerability, or deter or prevent the threat.
To illustrate these concepts with some examples, let us consider the following scenarios:
- A company has a website that generates revenue from online advertising. The website is an asset, and its value depends on the number of visitors and the quality of the content. The website has a vulnerability, which is a SQL injection flaw that allows attackers to execute malicious commands on the database. The threat is a hacker who wants to steal or delete the data, or deface the website. The risk is losing revenue, data, reputation, or customers.
- A student has a laptop that contains their personal and academic files. The laptop is an asset, and its value depends on the importance and sensitivity of the files. The laptop has a vulnerability, which is an outdated operating system that has known security holes. The threat is a virus that can infect the laptop through a USB drive, an email attachment, or a malicious website. The risk is losing or corrupting the files, or compromising the privacy or security of the student.
- A hospital has a network of medical devices that monitor and treat patients. The devices are assets, and their value depends on the health and safety of the patients. The devices have a vulnerability, which is a weak encryption algorithm that can be cracked by skilled attackers. The threat is a cybercriminal who wants to ransom or sabotage the devices, or a terrorist who wants to cause harm or chaos. The risk is endangering or harming the patients, or violating the laws or regulations.
These are just some of the possible examples of how threat, asset, vulnerability and risk can be defined and applied in different contexts. By understanding these concepts, one can better assess the current and future challenges of cybersecurity, and develop effective strategies and solutions to protect the assets from the threats.

