“Upmost importance” would describe a SIEM within an organization. Let’s do a high level view of what a SIEM is. “Security Information & Event Management” and its acronym is SIEM. Most SIEM come in form of software which is installed on a server, or multiple servers, and it primary function is to collect events from all critical devices on you network infrastructure. The secondary function of a SIEM is to allow analyst to perform search within the data collected by the SIEM. The third and final function of a SIEM is to perform automated search and reports, and provided alerts to security staff.
Sending the event logs
 Most information technology component (Servers, Routers, NAS, Firewall, Switches, Security Appliance..etc) that are manageable offer the capability to sent event logs to a Syslog server (Or SIEM). It is important, when selecting a device, to make certain it has the capacity to send its event logs to a server, as oppose to keeping the logs on in its own memory or storage. Depending on the type of device, an enormous amount of logs can be generated by the device, and it is better to have those logs handled by a specialized server (a SIEM) to avoid overloading the device itself. Log are usually sent in realtime or in small batches to the SIEM server over a specific network protocol.
Most information technology component (Servers, Routers, NAS, Firewall, Switches, Security Appliance..etc) that are manageable offer the capability to sent event logs to a Syslog server (Or SIEM). It is important, when selecting a device, to make certain it has the capacity to send its event logs to a server, as oppose to keeping the logs on in its own memory or storage. Depending on the type of device, an enormous amount of logs can be generated by the device, and it is better to have those logs handled by a specialized server (a SIEM) to avoid overloading the device itself. Log are usually sent in realtime or in small batches to the SIEM server over a specific network protocol.
Logs and Events
Think of log as Meta-Information (Information about information) which summarize the activities of a device. For example, A Firewall has all sorts of activities: Local & Remote Management, security policies, protocol routing, Unified Threat Management engines, Memory & CPU management, Storage, VPN services…etc. If an administrator logins the Firewall, make a policy change and then logouts of the firewall, an event will be registered for every action and sent to the SIEM server, and the information received will be placed in a SIEM Database and then processed by the SIEM’s filtering profile or event search tools.
A firewall logs can also include meta information of every packets transported through its various interface or Vlans. This type of logs is very important in attempts to understand, recreate and troubleshoot actions taken on or thru that Firewall. A device can also report to the SIEM any errors is encounters, this will be very useful to determine certain root cause of network issues.
Each events logged to a SIEM server contain detailed information about the origins of this event and when it was created. Therefor, an accurate timeshare is critical to properly use a SIEM.
Stamp that Time
When using a SIEM, and SIEM Server and every devices sending event logs to it need to have their internal clock synchronized, ideally to the milliseconds, otherwise, trying to collate events will be very difficult for an analyst. In less than a second, thousands or hundreds of thousand of event can be received by a SIEM server. So, if you are looking for an event that occurred between 10:11:25 pm and 10:11:28 pm which crashed the network, you will be very glad all devices have the same clock timestamp.
Clocks Sync
 Typically, each devices on your network have the capability to have their clocks (Time & Date) adjusted manually or automatically. To properly operate a SIEM, we need to (1) set each device time synchronization automatically using NTP (Network Time Protocol) and (2) use a very reliable Clock central server. In mission critical operation, it s not recommend to use public or (internet) NTP server to synchronize clocks. I would advise you consider investing in a GPS device which also offer NTP (Server) capabilities, and have ALL devices on your network use THAT network clock. You will be able to maintain milliseconds precisions for the majority of your events logged on your SIEM server.
Typically, each devices on your network have the capability to have their clocks (Time & Date) adjusted manually or automatically. To properly operate a SIEM, we need to (1) set each device time synchronization automatically using NTP (Network Time Protocol) and (2) use a very reliable Clock central server. In mission critical operation, it s not recommend to use public or (internet) NTP server to synchronize clocks. I would advise you consider investing in a GPS device which also offer NTP (Server) capabilities, and have ALL devices on your network use THAT network clock. You will be able to maintain milliseconds precisions for the majority of your events logged on your SIEM server.
SIEM Capacity
On any network, there is a LOT of noise generated by multiple services, protocols and devices. On a medium-Large network, a SIEM can easily receive hundreds of Gigabytes of events logs each day. This can become overwhelming and expensive if not managed properly. Things to consider when deploying a SIEM server(s):
i) How much event logs can your SIEM process (Store) per day.
ii) How long do you want (need) to retain those logs for later audit or search, which is often determined by your security audit policies and compliancy agreements.
iii) How much does a SIEM cost per Data store”
The last consideration can limit you ability to properly operate a SIEM server. Many SIEM software manufacturers sell their operating license based on how much data you send to it. A good way to limit this cost obstacle is to truly understand what type of logs you are sending to your SIEM server, and filter out non essential events. For example, there are hundreds of DHCP message and request sent on you network every minute, and you might not need to capture this type of information. Properly filtering and selecting when types of events you need to store in your SIEM can dramatically reduce its operation cost and database size. You will need the help of a “good” network engineer to properly set this up.
SSH vs HDD storage
![]() When cost is an issue, you want to Hard Disk Drives (HDD) to storage your SIEM database. A simple Raid array using HDD should be plenty and relatively reliable for all sorts of SIEM requirement. If cost is not an issue, I would recommend using Solid State Disk (SSD) to storage your search Database. The Primary Receiving SIEM could use HDD (To lower cost), and the secondary Search and Reporting SIEM could use SSD for optimum performance.
When cost is an issue, you want to Hard Disk Drives (HDD) to storage your SIEM database. A simple Raid array using HDD should be plenty and relatively reliable for all sorts of SIEM requirement. If cost is not an issue, I would recommend using Solid State Disk (SSD) to storage your search Database. The Primary Receiving SIEM could use HDD (To lower cost), and the secondary Search and Reporting SIEM could use SSD for optimum performance.
It is important to understand that the lifecycle of SSD drives is much shorter than typical HDD. SSD are use for Input/Output performance, but they tend to have short life spans. I would recommend using a proven disk array (RAID5 or better) if you plan to use SSD technology. If a SSD disk dies, you can replace that unit and quickly rebuild the disk without loosing any data.
SIEM on Cloud
Some companies offer a cloud based SIEM services. Instead of purchasing and operating your own SIEM device, you simply ship all your logs to their cloud servers and then access the SIEM console through a WebBrowser. Some companies offer value add feature to analyze and alert you when certain security condition have been detected in the logs received. These cloud based SIEM aren’t cheap either. Depending on your organization size, you might be better off hiring or delegating your SIEM management to your internal IT or Security staff.
CroudStrike is cloud based SIEM provider that I would consider first if I was looking for a Cloud based SIEM service. They have in-house security experts who can help you with any type of security events.
A proper SIEM architecture
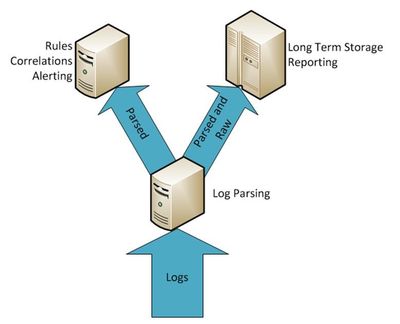 For medium to large networks, multiple SIEM servers will be required. For example, you might have a local SIEM server in each building on a university campus, which is often called (A Collector). Each SIEM will collect event logs from all devices within that building, then ship those logs to a central SIEM server. Them a central SIEM might copy (parse) its database in realtime to a secondary SIEM Server which is use for report or searches. Since reporting and search put a real heavy load on the server handling the Database, you don’t don’t want to place that type of load on principal SIEM Server, who is too busy receiving events from the collectors and/or devices.
For medium to large networks, multiple SIEM servers will be required. For example, you might have a local SIEM server in each building on a university campus, which is often called (A Collector). Each SIEM will collect event logs from all devices within that building, then ship those logs to a central SIEM server. Them a central SIEM might copy (parse) its database in realtime to a secondary SIEM Server which is use for report or searches. Since reporting and search put a real heavy load on the server handling the Database, you don’t don’t want to place that type of load on principal SIEM Server, who is too busy receiving events from the collectors and/or devices.
The power of SIEM
For example, a new employee complained to me that a Firewall web management portal was no longer accessible. After I asked him to describe to me what he did, he claimed he didn’t touch this firewall until he attempted to login using a Web browser.
After I troubleshooted and resolved the problem, I queried our SIEM server and investigate the root cause. It turns out that new employee lied to me about not having caused the problem in the first place simply because I could recreate the exact steps he originally took to login the firewall using SSH, then made a configuration mistake which locked out all Web management services. You wouldn’t imagine how many time people lied to me about events, and I unearthed the truth from the events storage on a SIEM.
With this in mind, understand that managing security of a network will quickly become reliant of a SIEM server (Infrastructure). Without the capability to go back in time and see what event took place, you will be blind and powerless to the past events.
Anyone serious about working in cybersecurity should first familiarize him/her self with SIEM technology. You can download basic Syslog servers (KIWI Log or GreyLogs), configure them and explore the features. Then work your way up large SIEM appliances. “Splunk”, a very popular SIEM software offer a demo unit which you can install on a Windows or Linux server and increase your understanding of SIEM technologies.
Since a SIEM server will probably be installed and managed by the IT department, you should focus on how to use a SIEM, build powerful filters, comprehensive reporting and useful alerts. This give you an advantage over other staff in quickly finding root cause of any types of events.
This was my view.
Cheers and Beers.

